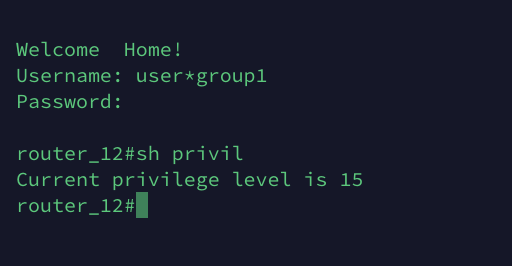
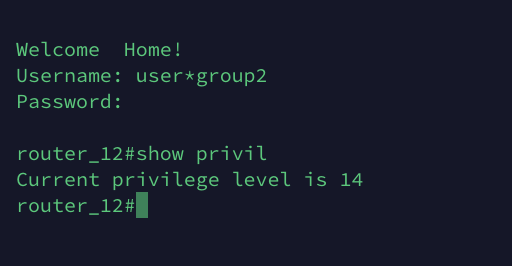
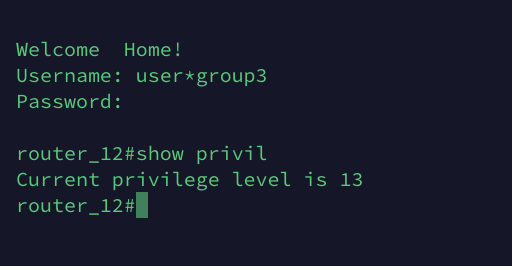
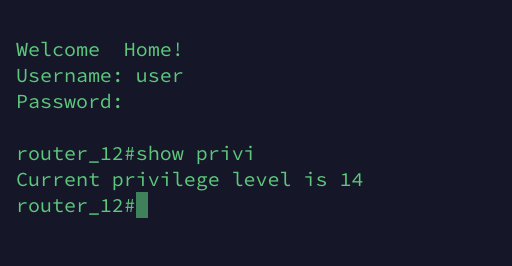
A TACACS user can be a member of several group, BUT! a user will be a member of only one general user group after login. A user can choose or switch user group while login. The best way to explain is to give you an example.
For example we have 3 user groups: